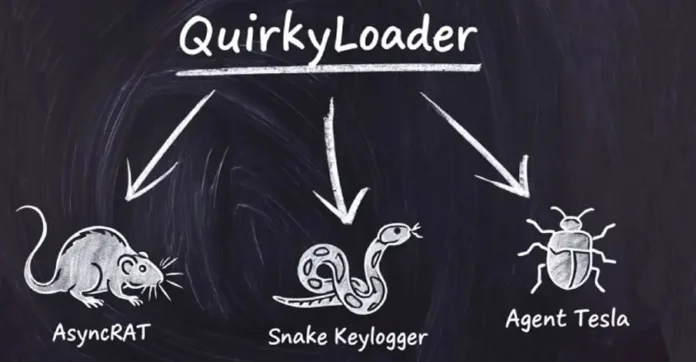
Cybersecurity experts have uncovered a new malware loader named QuirkyLoader, which has been actively used since November 2024 in email spam campaigns to deliver a range of malicious payloads. According to IBM X-Force, the loader has been linked to the distribution of several high-profile malware families, including Agent Tesla, AsyncRAT, Formbook, Masslogger, Remcos RAT, Rhadamanthys Stealer, and Snake Keylogger.
The attack method relies on spam emails sent through both legitimate providers and self-hosted servers. These emails carry malicious archive files containing a DLL, an encrypted payload, and a legitimate executable. Security researcher Raymond Joseph Alfonso explained, “The actor uses DLL side-loading, a technique where launching the legitimate executable also loads the malicious DLL. This DLL, in turn, loads, decrypts, and injects the final payload into its target process.” The payload is executed using process hollowing, typically injecting into AddInProcess32.exe, InstallUtil.exe, or aspnet_wp.exe.
IBM researchers noted that QuirkyLoader has been used in limited but targeted campaigns. In July 2025, two major operations were observed: one in Taiwan, which specifically targeted employees of Nusoft Taiwan, a network security firm, with Snake Keylogger, and another in Mexico, which appeared broader in scope, delivering Remcos RAT and AsyncRAT.
Alfonso highlighted that the DLL loader is consistently written in .NET languages and compiled ahead-of-time (AOT) into native machine code, giving it the appearance of being developed in C or C++, which complicates detection.
Rising Phishing Trends
Alongside QuirkyLoader, researchers are warning about evolving phishing tactics, particularly involving QR code phishing (“quishing”). Attackers have been embedding malicious QR codes inside emails, sometimes splitting them into parts or blending them with legitimate codes to bypass filters. “Malicious QR codes are popular with attackers for several reasons. They cannot be read by humans so don’t raise any red flags, and they can often bypass traditional security measures such as email filters and link scanners,” said Barracuda researcher Rohit Suresh Kanase.
Adding to the threat landscape, security firm NVISO Labs reported the emergence of a phishing kit linked to the PoisonSeed group. This kit impersonates login services from major platforms such as Google, SendGrid, and Mailchimp to steal credentials and two-factor authentication codes. The kit also uses precision-validated phishing, which verifies email addresses in real time before showing a fake login page, thereby increasing the success rate of credential theft.
Together, these developments underline how cybercriminals are rapidly refining their tactics — from malware loaders like QuirkyLoader to sophisticated phishing kits — to bypass defenses and target sensitive information worldwide.