Threat actors are actively exploiting a severe security vulnerability in the popular WordPress theme “Alone – Charity Multipurpose Non-profit”, potentially enabling complete control over affected websites. Tracked as CVE-2025-5394 and assigned a CVSS severity score of 9.8, this flaw has raised serious alarms within the WordPress community.
The vulnerability was identified and responsibly disclosed by security researcher Thái An, with detailed analysis provided by Wordfence, a leading WordPress security firm. The issue affects all versions of the theme up to and including 7.8.3, and was patched in version 7.8.5, released on June 16, 2025.
At the heart of the flaw is a function called alone_import_pack_install_plugin(), which lacks proper capability checks. This omission allows unauthenticated users to install plugins remotely via AJAX, leading to arbitrary file uploads and remote code execution.
“This vulnerability makes it possible for an unauthenticated attacker to upload arbitrary files to a vulnerable site and achieve remote code execution, which is typically leveraged for a complete site takeover,” said Wordfence’s István Márton.
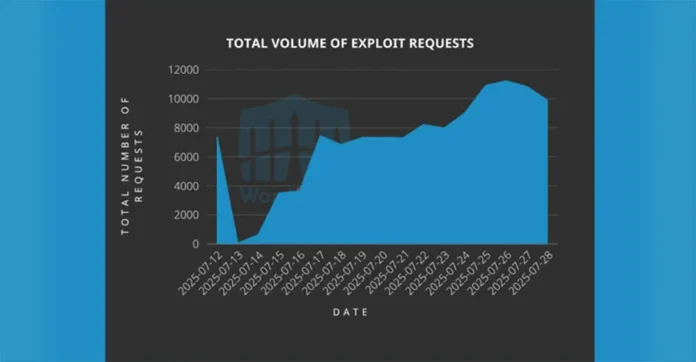
Exploitation of the flaw reportedly began as early as July 12, even before the vulnerability was made public, suggesting attackers were monitoring recent code changes for security loopholes. Wordfence has already blocked over 120,900 attack attempts, with malicious activity traced to several IP addresses including:
193.84.71.244
87.120.92.24
146.19.213.18
185.159.158.108
188.215.235.94
146.70.10.25
74.118.126.111
62.133.47.18
198.145.157.102
2a0b:4141:820:752::2
In the observed campaigns, attackers typically upload a ZIP archive—such as “wp-classic-editor.zip” or “background-image-cropper.zip”—containing PHP-based backdoors. These allow remote command execution, further file uploads, and creation of unauthorized administrator accounts, often using embedded file managers.
To reduce risk, WordPress administrators using the Alone theme should update immediately to version 7.8.5 or later. Site owners are also urged to check for unknown admin users, scan for suspicious files, and monitor access to /wp-admin/admin-ajax.php?action=alone_import_pack_install_plugin in their logs.