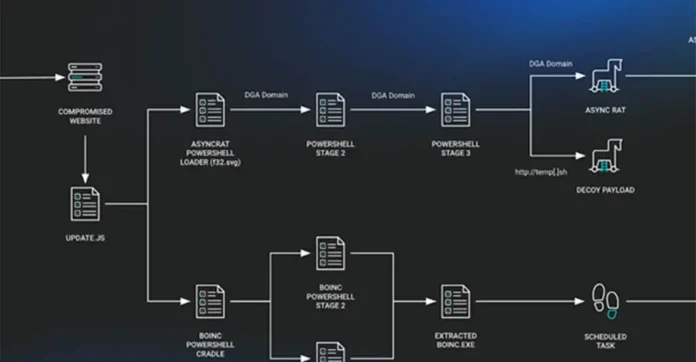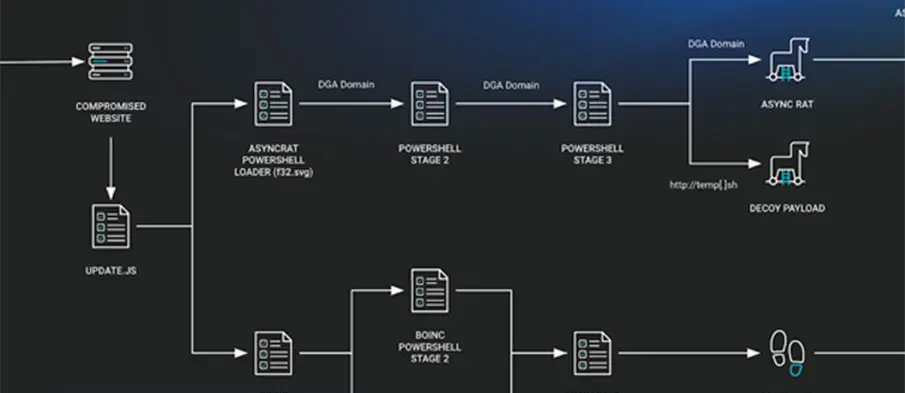
A new wave of SocGholish malware activity is exploiting Traffic Distribution Systems (TDSs) like Parrot TDS and Keitaro TDS to redirect unsuspecting users to malicious content, according to cybersecurity firm Silent Push. This development highlights the increasing sophistication of Malware-as-a-Service (MaaS) operations, where infected systems are sold to cybercriminal groups as initial access points.
SocGholish, also known as FakeUpdates, is a JavaScript loader malware that spreads through compromised websites, often disguised as fake browser updates for Chrome, Firefox, or other widely used applications. It’s attributed to the threat group TA569, also tracked as Gold Prelude, Mustard Tempest, and UNC1543.
Silent Push explains that “SocGholish infections typically originate from compromised websites”, with attackers either injecting malicious JavaScript directly or through intermediary files. The infection chain often ends with selling access to groups like Evil Corp, LockBit, Dridex, and Raspberry Robin, the latter of which has also been used to distribute SocGholish in recent campaigns.
A major enabler in this ecosystem is Keitaro TDS, a traffic filtering and redirection service. While it has legitimate uses, it has long been linked to malicious activities, from malware delivery to Russian influence operations. Keitaro dynamically filters users based on specific criteria and redirects high-value targets to SocGholish-controlled domains. Notably, Keitaro is believed to be connected to TA2726, a group that compromises websites and injects redirection links to serve paying clients.
“The intermediate C2 [command-and-control] framework dynamically generates payloads that victims download at runtime,” Silent Push noted. If a visitor doesn’t meet the attacker’s criteria, the framework halts the payload delivery.
Recent overlaps in malware delivery suggest that former operators of Dridex and Raspberry Robin may now be involved with SocGholish, sharing infrastructure and tactics. Concurrently, Zscaler has flagged an evolved version of Raspberry Robin with stronger obfuscation, a new Chacha-20 encryption system, and a privilege escalation exploit (CVE-2024-38196).
Meanwhile, campaigns distributing DarkCloud Stealer are on the rise. This malware is now delivered through phishing emails with embedded JavaScript and PowerShell loaders hidden in RAR files. It leverages process hollowing and DLLs embedded in JPEGs hosted on The Internet Archive, evading traditional defenses while harvesting credentials and financial data.
As these operations grow in scale and sophistication, security experts warn that defenders must evolve strategies to counter the increasingly modular, evasive, and AI-assisted threats emerging in today’s cybercrime landscape.