A financially driven cybercrime group identified as UNC5142 has been discovered leveraging blockchain smart contracts to distribute a range of information-stealing malware, including Atomic (AMOS), Lumma, Rhadamanthys (RADTHIEF), and Vidar, targeting both Windows and macOS systems.
According to Google Threat Intelligence Group (GTIG), “UNC5142 is characterized by its use of compromised WordPress websites and ‘EtherHiding,’ a technique used to obscure malicious code or data by placing it on a public blockchain, such as the BNB Smart Chain.” Google’s investigation revealed nearly 14,000 web pages infected with malicious JavaScript linked to UNC5142 as of June 2025, underscoring the group’s broad and indiscriminate targeting of vulnerable websites. No new activity has been observed since July 23, 2025, suggesting a potential operational shift or pause.
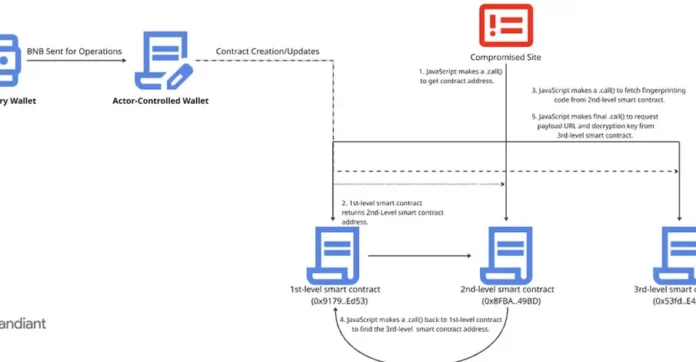
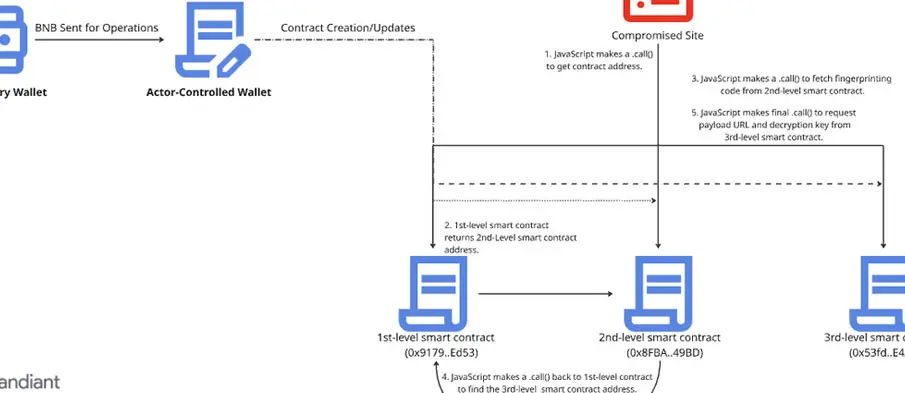
The EtherHiding technique first surfaced in October 2023, when Guardio Labs documented attacks that used Binance Smart Chain (BSC) contracts to deliver fake browser update warnings through compromised websites. Central to UNC5142’s campaigns is a multi-stage JavaScript downloader called CLEARSHORT, which facilitates the spread of malware through hijacked WordPress installations. The malware’s initial stage—embedded into website plugins, themes, or databases—retrieves additional payloads from malicious smart contracts hosted on the BNB Smart Chain.
These smart contracts then direct victims to CLEARSHORT landing pages using the ClickFix social engineering tactic, tricking users into executing malicious commands on Windows Run dialogs or macOS Terminal apps. Once executed, the malware installs stealer payloads retrieved from platforms such as GitHub or MediaFire.
GTIG’s analysis found that UNC5142 has continually refined its architecture, evolving from a single-contract to a three-contract system by late 2024 to improve agility and resilience. “This new architecture is an adaptation of a legitimate software design principle known as the proxy pattern, which developers use to make their contracts upgradable,” the report noted.
The updated Router-Logic-Storage setup allows attackers to modify elements like payload URLs or decryption keys without altering the compromised JavaScript code, making takedowns far more challenging. Updating a contract costs the attackers only $0.25 to $1.50 in network fees.
GTIG also identified two separate infrastructures — a Main system created in November 2024 and a Secondary one funded in February 2025 — suggesting organized scaling of their campaigns. Given the volume of infections, operational consistency, and range of deployed malware, Google assesses that UNC5142 has achieved notable success with this blockchain-powered cybercrime model.